
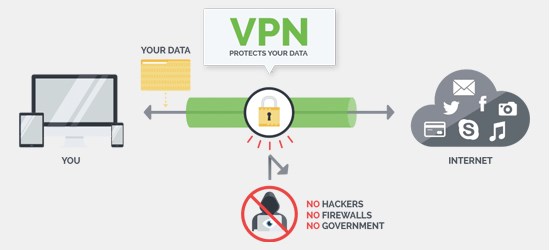
Elyzium VPNs establish encrypted connections through a public Internet access point. Securely connect using any of our VPN concentrators, routers, servers, or other third party VPN appliances. We deliver a comprehensive portfolio of network monitoring and management tools, interconnect solutions, and secure enterprise applications through our managed VPN services
All Elyzium VPN services are managed across the network--from the edge to the core or between data centers
Elyzium employs Internet Protocol Security (IPSec), Secure Sockets Layer (SSL), and Generic Routing Encapsulation (GRE) encryption methods and other VPN tunneling protocols to deliver reliable, secure VPN connections for network traffic.
When connected to the Internet, the Elyzium VPN router establishes a secure tunnel to a dedicated Elyzium VPN server/concentrator using high-level encryption and private key device identification. This allows traffic from an authorized network device attached to the Elyzium VPN router to traverse the Internet safely, securely, and encrypted at all times. The Elyzium VPN router also supports Dynamic Host Configuration Protocol (DHCP) for simple setup and installation.

ISP Service Provider in Gurgaon
||||||ISP Service Provider in Faridabad
||||||ISP Service Provider in Manesar
|Internet Service Provider in Delhi
|Internet Service Provider Services in Delhi
|Internet Service Provider in Gurgaon
|Internet Service Provider Services in Gurgaon
|Internet Service Provider in Noida
|Internet Service Provider Services in Noida
|Internet Service Provider in Faridabad
|Internet Service Provider Services in Faridabad
|Internet Service Provider in Sohna
|Internet Service Provider Services in Sohna
|||